Cloud Solutions
Cybersecurity
AI Agents
IT Consulting
Data & Analytics

Build in the Cloud - Without Compromising Security.
From startups to regulated enterprises, we help secure your cloud infrastructure, meet compliance mandates, and stay ahead of threats - without slowing you down.
Request a Security AssessmentThe Cloud Isn't Secure by Default.
Cloud platforms provide immense flexibility - but with flexibility comes risk. Misconfigurations, lack of visibility, and poor access controls are leading causes of cloud breaches. Our security-first approach ensures your systems are resilient, auditable, and protected at every layer.
Misconfigured Storage Buckets
Public S3 buckets and insecure storage settings can expose sensitive data to unauthorized access.
Overprivileged IAM Roles
Excessive permissions increase the blast radius when credentials are compromised.
Insecure APIs
Poorly secured API endpoints can allow attackers to access or manipulate your data and services.
Lack of Logging/Monitoring
Without proper visibility, breaches can go undetected for months, increasing damage and liability.
"80% of cloud breaches are caused by misconfiguration or human error."
We Secure Every Layer of Your Cloud Stack.
Our comprehensive security approach addresses vulnerabilities at every level, from infrastructure to application code.
Cloud Infrastructure Hardening
We lock down your cloud accounts with secure IAM, VPC segmentation, encryption, and hardened security groups and firewalls.
Compliance Framework Implementation
We help you align with industry standards such as SOC 2, ISO 27001, HIPAA, and GDPR - with technical controls, documentation, and readiness audits.
Security Audits & Risk Assessments
Get a detailed breakdown of vulnerabilities, misconfigurations, and potential risks across your infrastructure and workloads.
DevSecOps Integration
Shift security left by integrating tools like Snyk, Trivy, and Checkov into your CI/CD pipeline for early threat detection.
Cloud Security Posture Management (CSPM)
Gain visibility and control across your cloud environments with platforms like Prisma Cloud, Wiz, or AWS Security Hub.
Incident Response & Recovery Plans
We create tested, well-documented playbooks to ensure fast response and recovery in case of security incidents or data breaches.
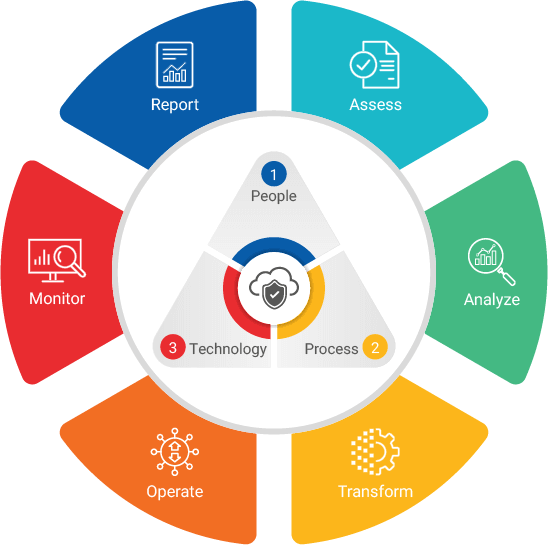
Security Isn't One-Off - It's Ongoing.
We implement a proven, iterative approach to build and maintain your security posture over time.
Discovery & Assessment
We analyze your current architecture, policies, and controls.
Threat Modeling & Gap Analysis
We identify weak points, attack surfaces, and compliance gaps.
Security Engineering & Automation
We implement technical controls like encryption, IAM policies, network ACLs, and integrate security tools into your workflows.
Monitoring, Alerts & Response
We set up dashboards, alerting mechanisms, and create documented incident response playbooks.
Compliance Tracking & Reporting
We help you maintain compliance posture through periodic checks, reporting tools, and automation.
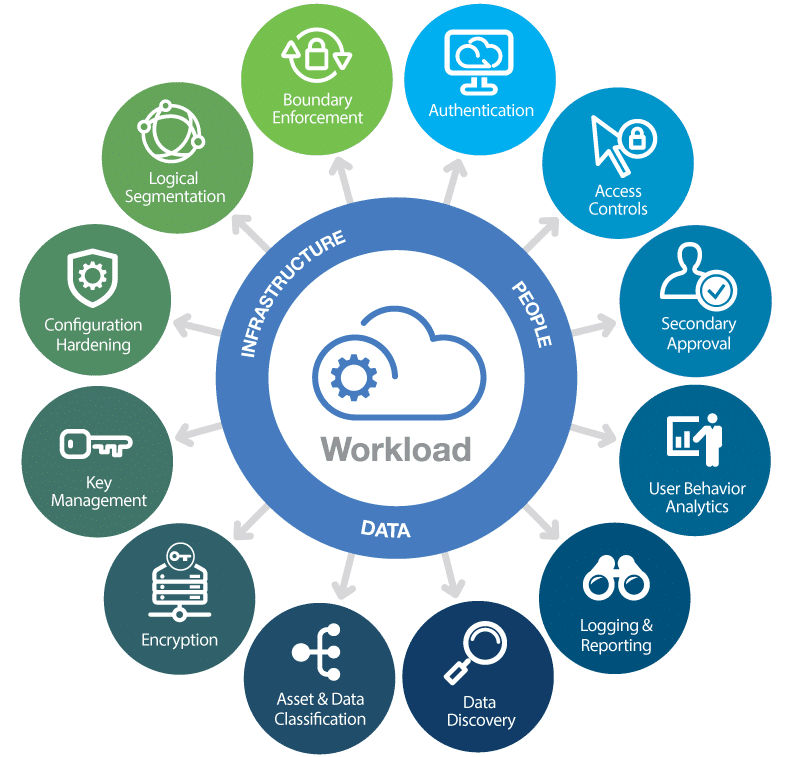
Compliance Doesn't Have to Be a Headache.
Whether you're pursuing SOC 2, ISO 27001, HIPAA, or GDPR, we simplify the process by mapping controls to real implementations, providing evidence-ready documentation, and preparing you for audits with confidence.

SOC 2
Trust Services Criteria for security, availability, processing integrity, and confidentiality.

ISO 27001
International standard for information security management systems (ISMS).

HIPAA
Healthcare compliance for protecting sensitive patient data.

PCI-DSS
Payment Card Industry Data Security Standard for handling credit card information.

GDPR
European Union's regulation on data protection and privacy.

NIST 800-53
Security and privacy controls for federal information systems and organizations.
"Cloud Amplify helped us achieve SOC 2 compliance in half the time we expected, with a systematic approach that made the process painless."
Built with the Best Tools in Cloud Security.
We combine native cloud tools with best-in-class security platforms to build tailored security solutions that match your tech stack and industry.